“Web 2.5”. BadgerDAO hack shows: half-decentralized = half-pregnant

At the start of December, someone drained funds from BadgerDAO users, stealing around $120 million. Almost enough to buy a PlayStation 5 off eBay.
So what, it’s a normal day in crypto. However, what’s interesting about this attack is that the smart contract part of it, the one that usually gets audited to death, worked perfectly well. The funds were stolen through the compromised UI, because despite everyone calling their dApps decentralized, most of the tech stack is still centralized:
- using centralized domains managed by ICANN and the domain registrar, that can be taken away by U.S. government (already happened) or compromised by hackers (bitcoin.org hacked in September)
- using centralized storage that can be modified by the cloud provider or completely removed (AWS nuking Parler, OVH data center catching on fire)
- using centralized proxies and CDNs like Cloudflare, with half of the internet trusting them (and whoever has access to it, like rogue employees and the NSA) with full permission to see all traffic and modify it in-flight
- accessing blockchains with browser extensions like Metamask and Phantom, which can be pulled from the web extension stores at any moment.
This is not the web3 we have been fighting for. This is not the next generation of the internet we have been dreaming about. And this is exactly why we have developed Point Network — the web3 framework that, for the first time, provides complete decentralization of the whole tech stack with the mantra — only decentralized domains, only decentralized storage, only decentralized identities.
In this post, we’ll rehash what happened with BadgerDAO, touch on why the internet is in such a dilemma in the first place, and finally, demonstrate how this could have and will be prevented by projects migrating to Point Network, the only virtual space which can be called web3.
What happened?
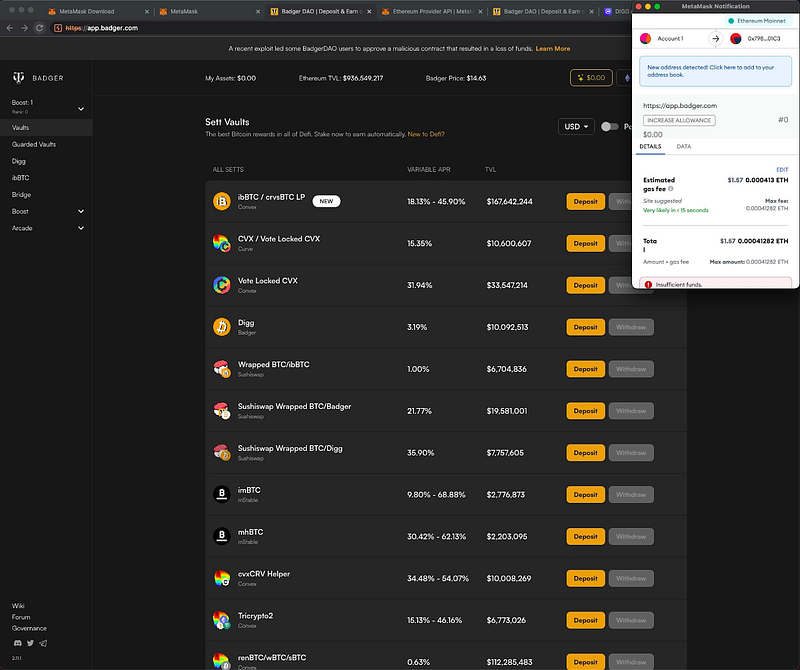
You can read the technical post-mortem report from BadgerDAO, but the gist of it is this:
- BadgerDAO uses Cloudflare, with Cloudflare’s servers sitting in between the website and its users. Nothing unusual, half the internet uses Cloudflare to ease the load on their servers and defend from DDoS attacks.
- Consequently, half the internet trusts Cloudflare servers to see all website traffic, modify it in-flight, and still be able to place that soothing green/grey padlock icon on your browser, because the padlock is now being manufactured by Cloudflare for each website.
- Unfortunately, Cloudflare had an insane vulnerability where an attacker could create a new account with someone else’s email, like bill.gates@microsoft.com, then without verifying the email generate API keys to access Cloudflare settings, and wait for the real Bill Gates to show up and complete the registration, with malicious API keys still active.
- This is what happened to BadgerDAO, according to the team. The next steps were trivial: use the API keys to modify JavaScript files on the website in such a way that when the transaction is generated and sent to your Metamask, it’s being replaced by a malicious one allowing the attacker to withdraw the funds.
Why are we here?
It’s easy to be quick to blame BadgerDAO or developers of other “d”Apps, but what are they to do, really?
Cloudflare is the de-facto standard for DDoS protection. You will invite more ridicule for not using it on any large project than for using it. The users have to access the application somehow, so you buy a domain name. And despite decentralized storage projects already existing, it’s non-trivial to not only store everything there, but verify that what the IPFS or Arweave gateways give you really hashes to the content ID you asked them about. And then there’s a bootstrapping problem: you still have to store the downloader-and-verifier code somewhere outside IPFS.
Developers working on web3 and moving further on the decentralization spectrum can be forgiven, because there hasn’t been any alternative, any technology that would decentralize everything. Until now.
Point Network: final push from Web 2.5 to Web 3
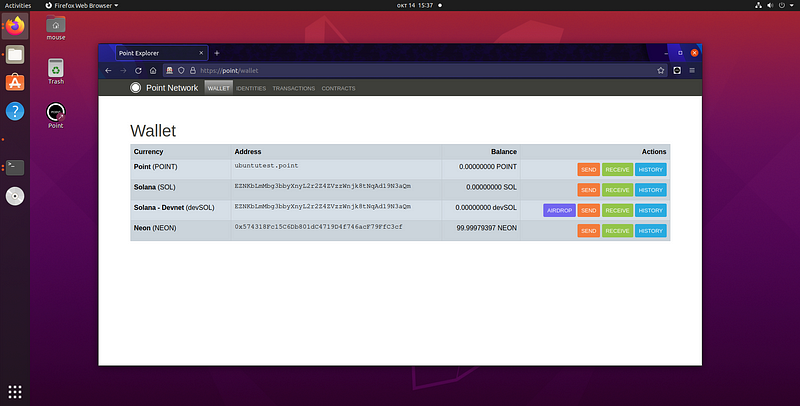
Point Network is a web 3.0 framework, aiming for radical decentralization. When you open Point Browser, you can’t access centralized domains like facebook.com or IP addresses, all connections to the legacy internet are severed. Instead, you can use:
- only decentralized domains—.point domains are stored on Point blockchain (using Solana as a base blockchain for now);
- only decentralized storage — developers won’t be able to pretend anymore that their application is decentralized, and then still use cloud providers. They are now forced to only reference files by hash that are deployed on the decentralized storage network Arweave; additionally, Point doesn’t blindly trust the gateways and still makes sure that the data integrity is preserved by verifying the data hashes;
- only decentralized identities — you won’t need millions of passwords on web3, you log into web3 with your seed phrase/private key, and are logged into every website automatically with your attached identity.
Someone might object: “but having decentralized websites would do nothing from stopping some developer’s keys from getting stolen and the website compromised, right?”
Well, not quite.
On Point Network, every update to a website is a transaction on the blockchain. This provides for insane flexibility in use cases.
One of them is holding the decentralized domain in a DAO multisig (short for multi-signature). So instead of centralized badger.com, BadgerDAO would have badger.point held in a multisig, meaning an update would need to be confirmed by, let’s say, 7 out of 20 developers.
As soon as the new update is pushed to decentralized Github by one of them, the rest would receive a notification, noticing the changes being sent, and the malicious update would not get past all of them and would be rejected, with $120M saved. And once you begin adding auditing companies into the multisig and compensate them in tokens, this can start looking like a really interesting workflow.
In addition to this, users on Point Network, due to the architecture described above, can be secured from:
- website censorship, because the domain could not be taken away from you, nor can the storage;
- identity/content censorship, because once you registered your account (identity) on web3, nobody can take it away from you;
- mass surveillance, with end-to-end encryption of private messages and emails based on public keys attached to identities (you know nothing has changed since Snowden revelations and all your emails and Zoom meetings are still being recorded and archived by the NSA, right?)
- and other forms of attack on our security and our privacy.
This is the web3 worth looking forward to, and working towards. All that is left is a little push from 2.5 to 3.0.
Interested to become a part of Point Network’s history and help us launch this together?
- You can help by spreading the word — clapping on the article, retweeting, usual stuff;
- We’re hiring! We’ve just got funded for the next round, and we’re looking for the best talent in the world to help us launch the beta in a few months. If you’re a developer with blockchain experience, please apply here. This will be much more fun and rewarding than whatever corporate CRM or ERP you’re working on, we promise! :)
- Sign up for updates by subscribing here on Medium, and to our Youtube channel, and Twitter
- And finally, come join the party and chat with us on Telegram! See you there 👋